Events
Foundry and IDC bring together IT decision-makers for must-attend technology events
Forging meaningful connections at 800+ events annually
IT executives are transformative leaders charged with driving business strategy. They trust us and depend on us for real solutions.
Leveraging 50+ years of IDG rich media brand industry expertise and relationships, our unique event content is delivered through the trusted lens of our world-class family of brands.
Ranging from multi-day educational symposiums and prestigious awards programs to intimate roundtable discussions, Foundry and IDC tailors the event type to deliver on audience objectives and needs.
Diverse events for different marketing strategies:
- Conferences and Summits
- Roundtables
- Dinners/Luncheons
- Awards and Leadership Events
- Custom

Foundry and IDC events businesses join forces in 2024
By combining our event content, delivery and audience development teams and capabilities under one unified global structure, Foundry and IDC can help you build an even greater pipeline of active IT buyers in 2024:
- More opportunities: now access 1,500 in-person and virtual events – delivered in local languages in over 70 countries and attended by more than 60,000 IT buyers
- Better targeting: whether your business specialises in cybersecurity, cloud, AI or any other major IT topic, we have grouped our events by topic and country/region to help you better target specific IT buyer communities that match your products, in your target markets.
- Greater value: by combining IDC and Foundry’s content expertise and marketing reach, we will draw an increased number of IT buyers to our events and deliver even more value for your event partnerships.
Generate new customers with Foundry and IDC events
Spanning across more than 40 countries, our array of 800+ events is strategically designed to captivate highly qualified audiences. These events serve as dynamic avenues for significant lead generation, all orchestrated by dedicated project managers who curate marketing campaigns tailored to your brand. Foundry and IDC events are thoughtfully designed to occur in-person, virtually, and through hybrid formats.

One of the most prestigious & coveted awards in technology
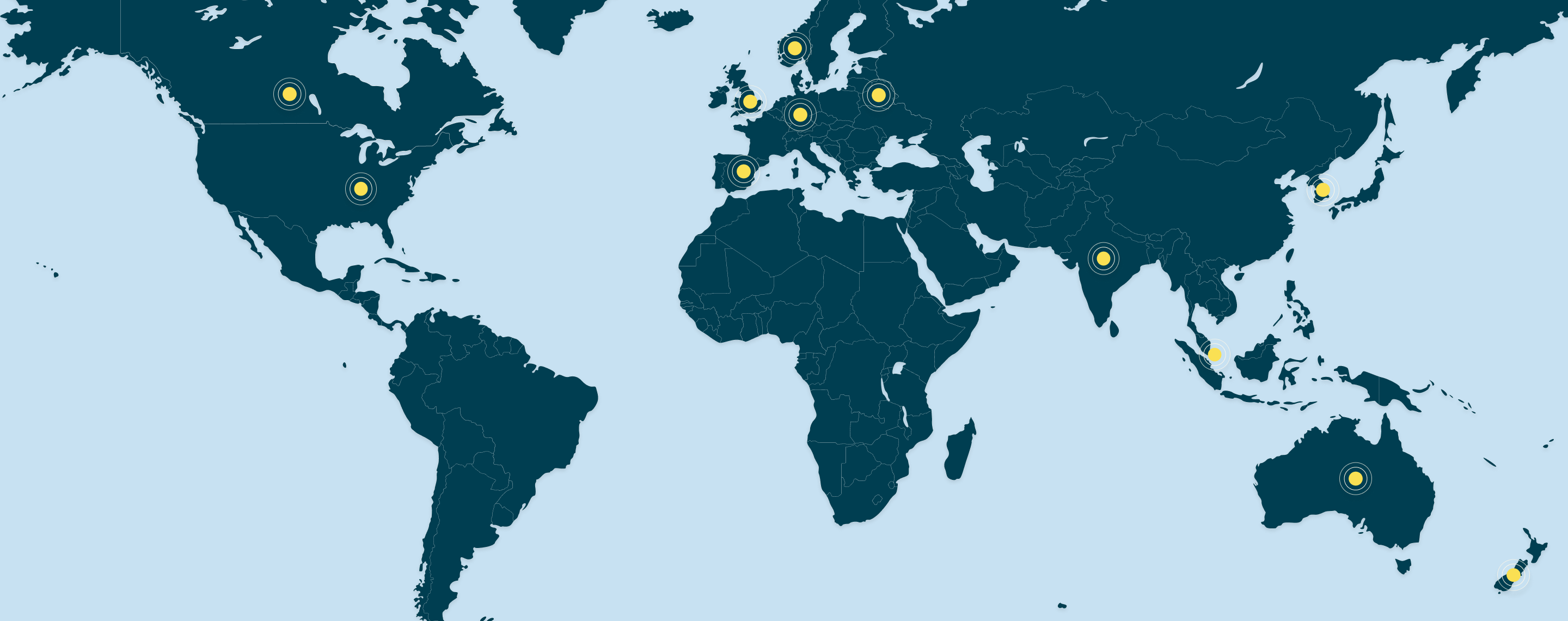
CIO 100 celebrates the achievements of top IT executives and their teams who are using IT in innovative ways to deliver business value, whether by creating competitive advantage, optimizing business processes, enabling growth, or improving relationships with customers. Awards programs and leadership summits take place in: The United States, Canada, United Kingdom, Spain, Singapore, Australia + NZ, Germany, India and Sweden.

Where risk is rewarded
CSO50 Conference + Awards are the premier conferences for information risk management and security. These events highlight how award-winning organizations are managing risk and information security. These events highlight where CSOs have found opportunities to expand their information security defenses and the technologies used to achieve success. Awards programs and conferences take place in: United States, United Kingdom, India, Australia + NZ.

Recognizing excellence in the Channel
ARN, Reseller News and Channel Asia celebrate excellence across the Australian, New Zealand and ASEAN tech channels. Our programs acknowledge the achievements of talented teams who have become influential figures across the channel partner ecosystem. The Women in ICT Awards (WIICTA) was first launched in Australia in 2012, by ARN, celebrating gender diversity and recognizing female excellence across the channel.

Virtual or live: Meet prospects where they want to engage
IT decision makers attend events virtually as well as in person. Content relied on the most during the purchase process can be achieved directly at virtual events, such as product demos, vendor presentations, and analyst research.
Your only partner for IT events
Upcoming events
Our global events portfolio is designed to connect buyers and sellers of technology.

IDC Qatar Hybrid Cloud Roadshow 2024
1 day, 80 – 100 attendees

Digital Enterprise Forum Denmark
1 day, 50+ attendees
FutureIT Boston
AI, Data and Tech Leadership: Finding business value from emerging tech innovations | Boston
Future IT, a series of in-person, one-day regional events bring ITDMs, industry leaders and leading solution providers together to network and learn about topics such as cloud computing, cybersecurity, and digital transformation.
FutureIT Chicago
AI, Data and Tech Leadership: Finding business value from emerging tech innovations | Chicago
Future IT, a series of in-person, one-day regional events bring ITDMs, industry leaders and leading solution providers together to network and learn about topics such as cloud computing, cybersecurity, and digital transformation.
CSO’s SecureIT New York
New York
SecureIT is an in-person, one-day regional event that brings ITDMs, industry leaders and leading solution providers together to network and learn about topics such as cybersecurity and digital transformation.
Sponsorships at our events provides high-value visibility and interaction. Build relationships with decision makers while driving awareness of your brand.
Foundry and IDC’s events provide exceptional opportunities to learn from and network with top IT professionals from industry-leading organizations.
Interested in sharing your expertise with an eager audience? We have a variety of speaking opportunities.